Mostrando entradas con la etiqueta linux. Mostrar todas las entradas
git stash
save changes in stash with message and interactive changes
list changes in stash
get from stash at position 0 witout remove register the stash
get from stash at position 0 remove register the stash
get from stash at position 0 remove register the stash
manually stash
save changes in stash with message and interactive changes
Terminal:
git stash save -p -m "custom message"
list changes in stash
Terminal:
git stash list
get from stash at position 0 witout remove register the stash
Terminal:
git stash apply --index 0
get from stash at position 0 remove register the stash
Terminal:
git stash pop 0
get from stash at position 0 remove register the stash
Terminal:
git stash drop 0
manually stash
Terminal:
man git stash
kscreenlocker nvidia fix
first disable compositor and change to OpenGL3.1
disable image of lockscreen
disable blur
search: WallpaperFaderadd attribute if dont exist or change value
visible: false
first disable compositor and change to OpenGL3.1
disable blur
Terminal:
nano /usr/share/plasma/look-and-feel/org.kde.breeze.desktop/contents/lockscreen/LockScreenUi.qml
visible: false
looking delay loading booting GNU/Linux
looking blame process delay booting
looking dependent process
looking blame process delay booting
Terminal:
systemd-analyze blame
looking dependent process
Terminal:
systemctl show -p Requires lvm2-monitor.service
Terminal:
systemctl disable NetworkManager-wait-online.service
remove logo when loading GNU/Linux system
if you want see all services starting when loading your system then do this:
in variable
and remove of only
run this command
if you want see all services starting when loading your system then do this:
Terminal:
nano /etc/default/grub
in variable
Terminal:
GRUB_CMDLINE_LINUX_DEFAULT=
and remove of only
Terminal:
quiet splash
run this command
Terminal:
update-grub
How to disable keyring in Manjaro
install manage keyring
search the application
change the password keyring (sorry for the picture are ubuntu, but seahorse is same application)
write old password
now type password in blank
accept use unencrypted passwords
That’s it! Restart your computer for the setting to take effect. Next time you launch Chrome or Chromium browser, you should not see keyring request.
Source: https://www.fosslinux.com/2561/how-to-disable-keyring-in-ubuntu-elementary-os-and-linux-mint.htm
install manage keyring
Terminal:
sudo pacman -S seahorse
search the application
change the password keyring (sorry for the picture are ubuntu, but seahorse is same application)
write old password
now type password in blank
accept use unencrypted passwords
That’s it! Restart your computer for the setting to take effect. Next time you launch Chrome or Chromium browser, you should not see keyring request.
Source: https://www.fosslinux.com/2561/how-to-disable-keyring-in-ubuntu-elementary-os-and-linux-mint.htm
configure cpupower
check type driver
if is intel_pstate
you should be this:
replace for this:
GRUB_CMDLINE_LINUX_DEFAULT="quiet intel_pstate=disable "
you need restart the computer
when start yout computer again
check changes
make permanent configuration
restart you computer
check changes
install tool
script disable turbo-boost cpu
https://gitlab.com/cirelramos/oh-my-zsh/raw/master/turbo-boost.sh
change permisson execute
execute enable
check changes
Manager cpupower
Source:
https://wiki.archlinux.org/index.php/CPU_frequency_scaling_(Espa%C3%B1ol)
https://unix.stackexchange.com/questions/424602/is-it-possible-to-set-a-constant-lowest-cpu-frequency-under-the-modern-pstate
https://lenovopress.com/lp0826.pdf
https://askubuntu.com/questions/613498/automatic-switching-between-performance-and-powersave-mode-on-plugging-in-out-th
Terminal:
sudo pacman -S cpupower
Terminal:
systemctl start cpupower && systemctl enable cpupower
check type driver
Terminal:
cat /sys/devices/system/cpu/cpu*/cpufreq/scaling_driver
you should be this:
Terminal:
nano /etc/default/grub
replace for this:
GRUB_CMDLINE_LINUX_DEFAULT="quiet intel_pstate=disable "
Terminal:
sudo update-grub
you need restart the computer
Terminal:
sudo reboot
when start yout computer again
Terminal:
sudo cpupower frequency-set -d 1.20Ghz -u 2.20Ghz -g powersave -rand should be change the frequency and gobernator
check changes
Terminal:
cpupower frequency-info
make permanent configuration
Terminal:
sudo nano /etc/default/cpupower
restart you computer
Terminal:
sudo reboot
check changes
Terminal:
cpupower frequency-info
BONUS
install tool
Terminal:
sudo pacman -S msr-tools
script disable turbo-boost cpu
https://gitlab.com/cirelramos/oh-my-zsh/raw/master/turbo-boost.sh
change permisson execute
Terminal:
sudo chmod +x ~/turbo-boost.sh
execute disable
Terminal:
sudo ~/.oh-my-zsh/turbo-boost.sh disable
execute enable
Terminal:
sudo ~/.oh-my-zsh/turbo-boost.sh enable
check changes
Terminal:
cpupower frequency-info
Manager cpupower
Source:
https://wiki.archlinux.org/index.php/CPU_frequency_scaling_(Espa%C3%B1ol)
https://unix.stackexchange.com/questions/424602/is-it-possible-to-set-a-constant-lowest-cpu-frequency-under-the-modern-pstate
https://lenovopress.com/lp0826.pdf
https://askubuntu.com/questions/613498/automatic-switching-between-performance-and-powersave-mode-on-plugging-in-out-th
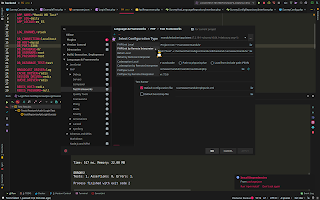
phpstorm php cli remote interpreter with docker 2019
connect to docker
configure cli interpeter
configure image
configure remote interprete
global config
or specifc network
run testunit
composer
phpunit
test result
connect to docker
configure cli interpeter
configure image
configure remote interprete
global config
or specifc network
run testunit
composer
phpunit
test result
SSH Passwordless Login Using SSH Keygen in 5 Easy Steps
Step 1: Create Authentication SSH-Kegen Keys on – (192.168.0.12)
Step 1: Create Authentication SSH-Kegen Keys on – (192.168.0.12)
First login into server 192.168.0.12 with user tecmint and generate a pair of public keys using following command.
Terminal:
ssh-keygen -t rsa
Step 2: Create .ssh Directory on – 192.168.0.11
Use SSH from server 192.168.0.12 to connect server 192.168.0.11 using sheena as user and create .sshdirectory under it, using following command.
Terminal:
ssh sheena@192.168.0.11 mkdir -p .ssh
Step 3: Upload Generated Public Keys to – 192.168.0.11Use SSH from server 192.168.0.12 and upload new generated public key (id_rsa.pub) on server 192.168.0.11under sheena‘s .ssh directory as a file name authorized_keys.
Terminal:
cat .ssh/id_rsa.pub | ssh sheena@192.168.0.11 'cat >> .ssh/authorized_keys'
Step 4: Set Permissions on – 192.168.0.11Due to different SSH versions on servers, we need to set permissions on .ssh directory and authorized_keys file
Terminal:
ssh sheena@192.168.0.11 "chmod 700 .ssh; chmod 640 .ssh/authorized_keys"
Step 5: Login from 192.168.0.12 to 192.168.0.11 Server without Password
Terminal:
ssh sheena@192.168.0.11
remove metadata file with linux terminal
install package
all files a folder
Fuente: https://askubuntu.com/questions/26911/erase-and-rewrite-mp3-id3-tags
install package
Terminal:
sudo apt-get install id3v2
check metadata just now
Terminal:
id3v2 -l some_file.mp3
erease metada
Terminal:
id3v2 -s some_file.mp3
erease metada
Terminal:
id3v2 -s some_file.mp3
all files a folder
Terminal:
for i in *.mp3; do echo "Processing $i"; id3v2 -s "$i"; done
Fuente: https://askubuntu.com/questions/26911/erase-and-rewrite-mp3-id3-tags
arch and manjaro temp size
create this script and run:
source: https://gist.github.com/ertseyhan/618ab7998bdb66fd6c58
create this script and run:
Terminal:
#!/bin/bash
sudo mount -o remount,size=40G,noatime /tmp
echo "Done. Please use 'df -h' to make sure folder size is increased."
source: https://gist.github.com/ertseyhan/618ab7998bdb66fd6c58
how create service linux repeat each 10s
Source:
https://unix.stackexchange.com/questions/198444/run-script-every-30-min-with-systemd
Terminal:
nano /etc/systemd/system/test.service
[Unit]
Description=test_job
[Service]
Type=oneshot
ExecStart=/usr/bin/php /tmp/run.php
Terminal:
nano /etc/systemd/system/test.timer
[Unit]
Description=test
[Timer]
OnUnitActiveSec=10s
OnBootSec=10s
[Install]
WantedBy=timers.target
Terminal:
systemctl daemon-reload
Terminal:
systemctl start test.timer
Terminal:
systemctl list-timers --all
Source:
https://unix.stackexchange.com/questions/198444/run-script-every-30-min-with-systemd
how to connect your home server to a domain with cloudflare
this tutorial is very extend for has various points:
well cloudflare is a server dns that allows you to manage our dns for free for the domains we use and create sub-domains, although it has more cloudflare tools, we will use some of them
after you register:
1. Add the site
select plan to use:
when you finalize the purchase for 0$ you can see that:
press to button continue
now you must change dns nameserver in your domain
for example in my domain https://my.freenom.com/
change to Name-servers
to
check the name-servers is working
2. Auto update your dynamic ip
if you have a dynamic ip, you need send the new ip to cloudflare for this use a small script bash for run with crontab in Gnu/Linux the best system :)
well for this we looking 3 elements
a) api key
b) id zone dns (for domain)
c) id domain in zone dns
now we use curl and api for get the id domain
https://api.cloudflare.com/
list dns records
https://api.cloudflare.com/#dns-records-for-a-zone-list-dns-records
get the attribute id and use after dns_record at url
you remember get the id of your domain example ramdontest.ml, the others are sub-domain and we interest update only the domain because the sub-domain has the same ip, because use dns type CNAME
update the ip
script bash
3. Add sub-domains to domain
Add the sub-domain
this is very important, change the domain to dns only, this is you can connect for ssh with domain or you can a sub-domain change to dns only and connect to ssh
Example:
4. Select to type of encryption
These options are listed from least (Off) to most secure (Full SSL (Strict)). All options are available in all customer plans.
Off: No secure connection between your visitor and Cloudflare, and no secure connection between Cloudflare and your web server either. This means that visitors can only view your website over HTTP, and any visitor attempting to connect via HTTPS will receive a HTTP 301 Redirect to the plain HTTP version of your website.
Flexible SSL: A Secure connection between your visitor and Cloudflare, but no secure connection between Cloudflare and your web server. You don't need to have an SSL certificate on your web server, but your visitors still see the site as being HTTPS enabled. This option is not recommended if you have any sensitive information on your website. This setting will only work for port 443->80, not for the other ports we support like 2053. It should only be used as a last resort if you are not able to setup SSL on your own web server. Be aware it can cause issues when you decide to switch away from it: How do I fix the infinite redirect loop...
Full SSL: A secure connection between your visitor and Cloudflare, plus a secure connection (but not authenticated) between Cloudflare and your web server. You will need to have your server configured to answer HTTPS connections, with at least a self-signed certificate. The authenticity of the certificate is not verified: from Cloudflare’s point of view (when we connect to your origin web server), it’s the equivalent of bypassing this error message. But as long as the address of your origin web server is correct in your DNS settings, you know that we’re connecting to your web server, and not someone else’s.
Full SSL (Strict): A secure connection between your visitor and Cloudflare, plus a secure and authenticated connection between Cloudflare and your web server. You will need to have your server configured to answer HTTPS connections, with a valid SSL certificate. This certificate must be signed by a certificate authority that is trusted by Cloudflare, have an expiration date in the future, and respond for the request domain name (hostname). If you've added a CNAME record for the hostname on Cloudflare, the certificate's Common Name or SAN may also match the CNAME target.
Strict (SSL-Only Origin Pull): Enterprise only This mode has the same certificate requirements as Full (Strict) and will also upgrade all connections between Cloudflare and the origin from HTTP to HTTPS, even if the original content requested is over HTTP.
Origin CA certificates, generated by Cloudflare, can be used with either the Full or Full(strict) options as they are trusted by Cloudflare. You can find more information about Origin CA certificates below:
if you want use Flexible SSL dont need config more, whole is ready.
now configuration with full mode
select to full mode
create certificate
copy the code pem and code key and paste in your server
you should have this
5. Configuration encryption pem and key with nginx
links: https://support.cloudflare.com/hc/en-us/articles/200170416-What-do-the-SSL-options-mean-
this tutorial is very extend for has various points:
- Add site
- Auto update your dynamic ip
- Add sub-domains to domain
- Select to type of encryption
- Configuration encryption pem and key with nginx
well cloudflare is a server dns that allows you to manage our dns for free for the domains we use and create sub-domains, although it has more cloudflare tools, we will use some of them
after you register:
1. Add the site
select plan to use:
when you finalize the purchase for 0$ you can see that:
press to button continue
now you must change dns nameserver in your domain
for example in my domain https://my.freenom.com/
change to Name-servers
to
check the name-servers is working
2. Auto update your dynamic ip
if you have a dynamic ip, you need send the new ip to cloudflare for this use a small script bash for run with crontab in Gnu/Linux the best system :)
well for this we looking 3 elements
a) api key
b) id zone dns (for domain)
c) id domain in zone dns
now we use curl and api for get the id domain
https://api.cloudflare.com/
list dns records
https://api.cloudflare.com/#dns-records-for-a-zone-list-dns-records
get the attribute id and use after dns_record at url
Terminal:
curl -X GET "https://api.cloudflare.com/client/v4/zones/YOUR_ZONE_ID/dns_records?type=A&name=YOUR_DOMAIN" -H "X-Auth-Email: YOUR_EMAIL" -H "X-Auth-Key: YOUR_API_KEY" -H "Content-Type: application/json"
you remember get the id of your domain example ramdontest.ml, the others are sub-domain and we interest update only the domain because the sub-domain has the same ip, because use dns type CNAME
update the ip
Terminal:
curl -X PUT "https://api.cloudflare.com/client/v4/zones/YOUR_ZONE_ID/dns_records/YOUR_ID_DOMAIN" \ -H "X-Auth-Email: user@example.com" \ -H "X-Auth-Key: YOUR_API_KEY" \ -H "Content-Type: application/json" \ --data '{"type":"A","name":"example.com","content":"127.0.0.1","ttl":1,"proxied":false}'the word or number with red is because you change 1 to 120 or true - false, for balance with cloudflare or without balance
script bash
Terminal:
#!/bin/sh ipNow=$(/sbin/ifconfig enp2s0 | grep -i 'Direc. inet' | cut -d ":" -f 2 | cut -d " " -f 1) ipOld="" UBICATION_LOGS="/opt/logs/" ejecutarCodigo() { { echo "From: Server Update IP <server@YOUR-DOMAIN.COM>" echo "Sender: YOUR-MAIL@GMAIL.COM" echo "To: YOUR-MAIL@GMAIL.COM" echo "Subject: The server change ip" echo echo "The server change ip "$ipOld" to "$ipNow } | /usr/sbin/ssmtp YOUR-MAIL@gmail.com #enviar email } while read line; do ipOld=$line done <$UBICATION_LOGS"ipOld.js" echo $ipOld" - "$ipNow if [ $ipOld != $ipNow ]; then #loadwebs.tk curl -X PUT "https://api.cloudflare.com/client/v4/zones/YOUR_ID_ZONE/dns_records/YOUR_ID_DOMAIN" \ -H "X-Auth-Email: YOUR-MAIL@gmail.com" \ -H "X-Auth-Key: YOUR_API_KEY" \ -H "Content-Type: application/json" \ --data '{"type":"A","name":"YOUR_DOMAIN","content":'\"$ipNow\"',"ttl":1,"proxied":false}' ejecutarCodigo else echo "NO" fi
3. Add sub-domains to domain
this is very important, change the domain to dns only, this is you can connect for ssh with domain or you can a sub-domain change to dns only and connect to ssh
Example:
4. Select to type of encryption
These options are listed from least (Off) to most secure (Full SSL (Strict)). All options are available in all customer plans.
Off: No secure connection between your visitor and Cloudflare, and no secure connection between Cloudflare and your web server either. This means that visitors can only view your website over HTTP, and any visitor attempting to connect via HTTPS will receive a HTTP 301 Redirect to the plain HTTP version of your website.
Flexible SSL: A Secure connection between your visitor and Cloudflare, but no secure connection between Cloudflare and your web server. You don't need to have an SSL certificate on your web server, but your visitors still see the site as being HTTPS enabled. This option is not recommended if you have any sensitive information on your website. This setting will only work for port 443->80, not for the other ports we support like 2053. It should only be used as a last resort if you are not able to setup SSL on your own web server. Be aware it can cause issues when you decide to switch away from it: How do I fix the infinite redirect loop...
Full SSL: A secure connection between your visitor and Cloudflare, plus a secure connection (but not authenticated) between Cloudflare and your web server. You will need to have your server configured to answer HTTPS connections, with at least a self-signed certificate. The authenticity of the certificate is not verified: from Cloudflare’s point of view (when we connect to your origin web server), it’s the equivalent of bypassing this error message. But as long as the address of your origin web server is correct in your DNS settings, you know that we’re connecting to your web server, and not someone else’s.
Full SSL (Strict): A secure connection between your visitor and Cloudflare, plus a secure and authenticated connection between Cloudflare and your web server. You will need to have your server configured to answer HTTPS connections, with a valid SSL certificate. This certificate must be signed by a certificate authority that is trusted by Cloudflare, have an expiration date in the future, and respond for the request domain name (hostname). If you've added a CNAME record for the hostname on Cloudflare, the certificate's Common Name or SAN may also match the CNAME target.
Strict (SSL-Only Origin Pull): Enterprise only This mode has the same certificate requirements as Full (Strict) and will also upgrade all connections between Cloudflare and the origin from HTTP to HTTPS, even if the original content requested is over HTTP.
Origin CA certificates, generated by Cloudflare, can be used with either the Full or Full(strict) options as they are trusted by Cloudflare. You can find more information about Origin CA certificates below:
if you want use Flexible SSL dont need config more, whole is ready.
now configuration with full mode
select to full mode
create certificate
copy the code pem and code key and paste in your server
you should have this
5. Configuration encryption pem and key with nginx
Terminal:
server { listen 443 ssl; server_name first.ramdontest.ml; root /var/www; index index.php index.html index.htm index.nginx-debian.html; ssl_certificate /opt/ssl/ramdontest.pem; ssl_certificate_key /opt/ssl/ramdontest.key; access_log /opt/logs/ramdontest.ml.access_log.js; error_log /opt/logs/ramdontest.ml.error_log.js; rewrite_log on; location / { proxy_pass http://localhost:3202; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection 'upgrade'; } }
links: https://support.cloudflare.com/hc/en-us/articles/200170416-What-do-the-SSL-options-mean-
Suscribirse a:
Entradas
(
Atom
)


















































































.svg.png)
